Deploy Lambda via AWS CLI or Console
Create an AWS Lambda Function
- Via Console:
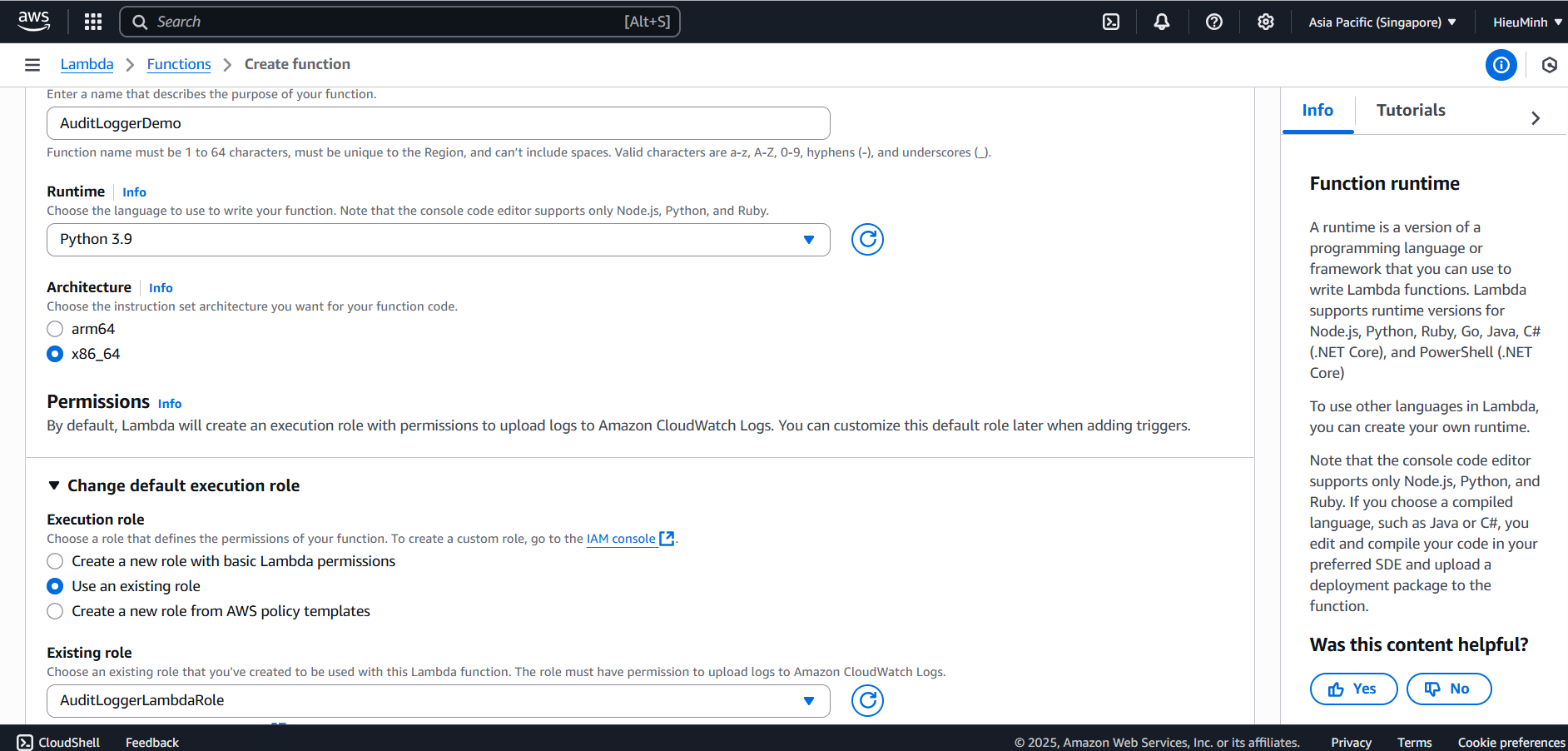
- AWS Console: navigate to Lambda → Functions → Create function.
- Function name: AuditLoggerDemo
- Runtime: Python 3.9
- Architecture: x86_64
- Permissions: Open Change default execution role → Select Use an existing role -> AuditLoggerLambdaRole.
- Click Create function.
- On the new function page:
- Code Source:
- Select Upload from → .zip file.
- Upload the function.zip file (containing audit_logger.py).
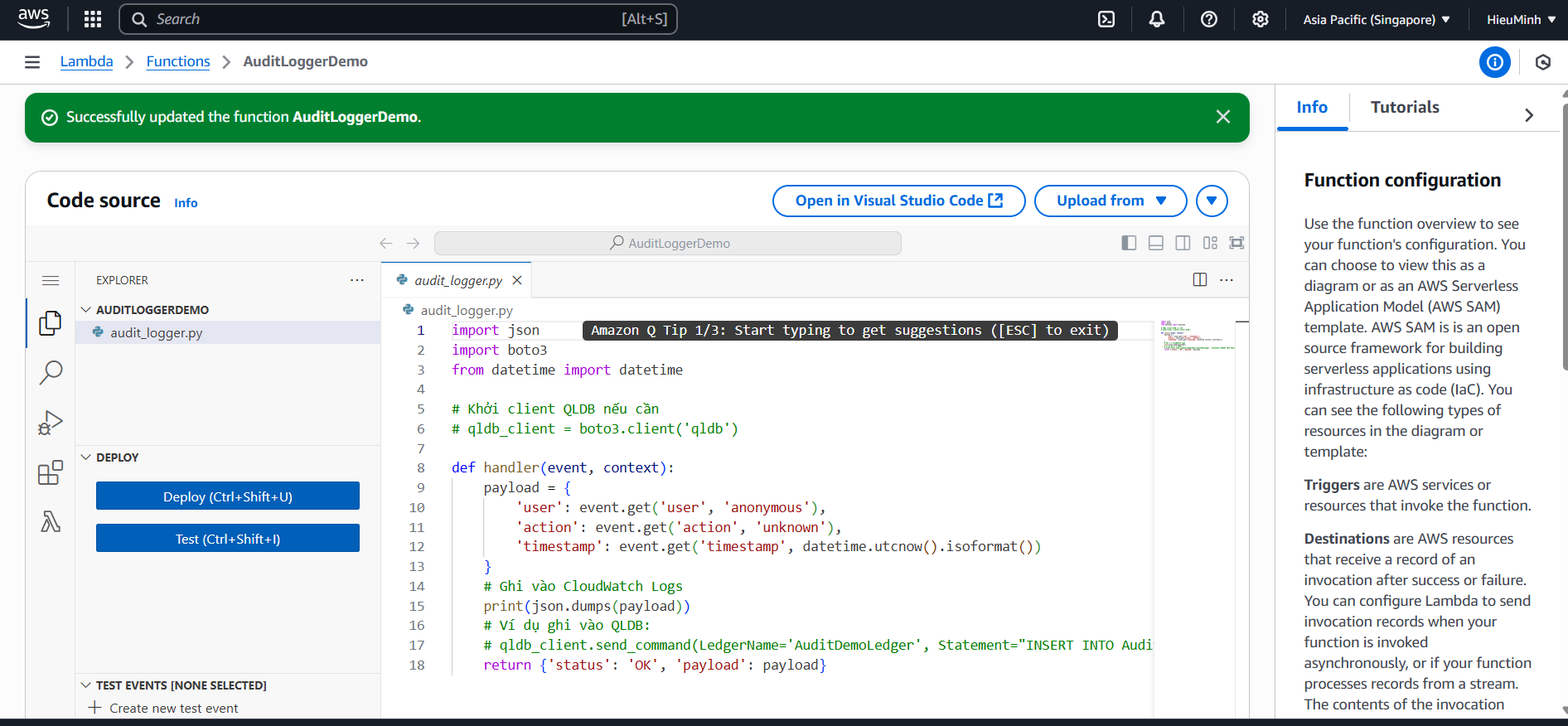
- Deploy the code.
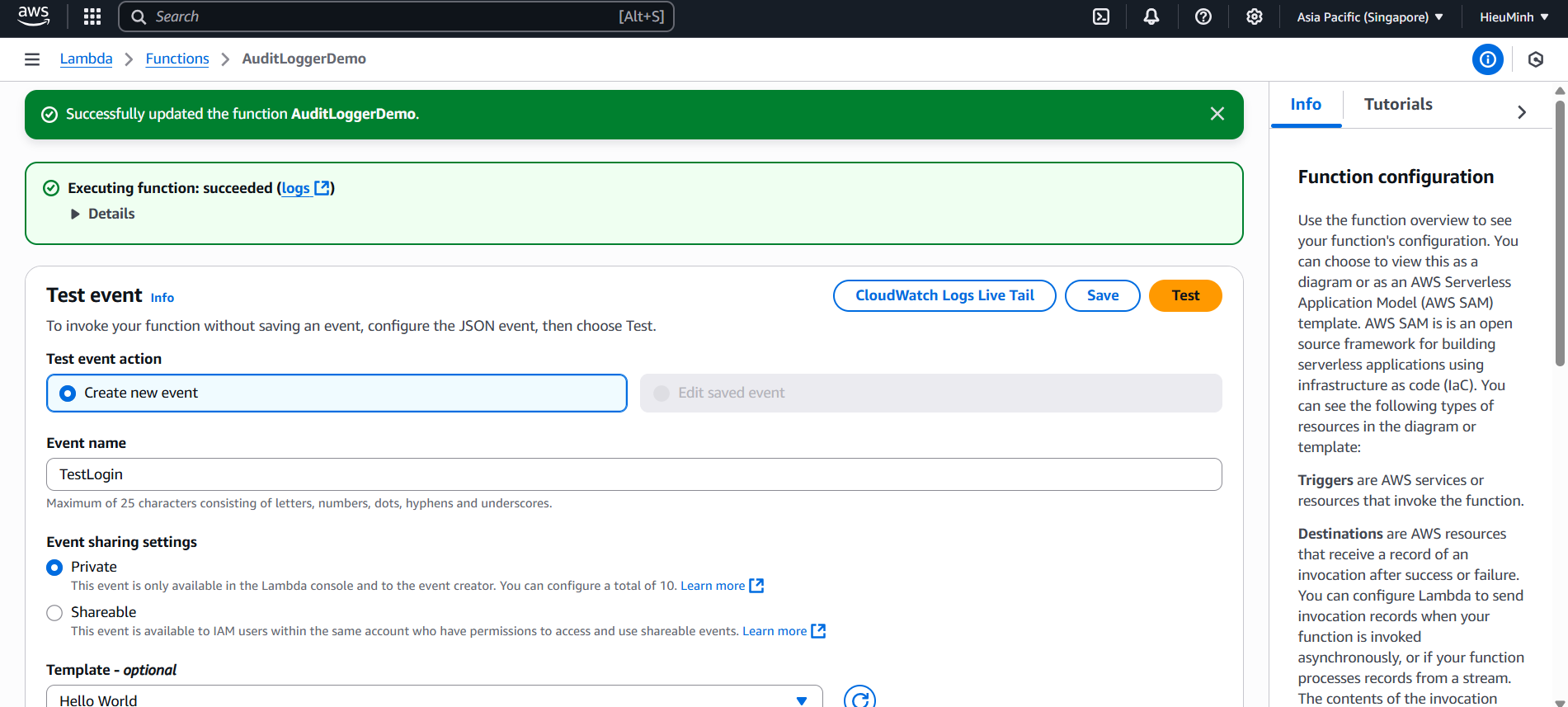
- Test event
- In the Test tab
- Set Event name: TestLogin
- Paste the JSON:
{“user”:“hocsinh1”,“action”:“login”,“timestamp”:“2025-07-27T12:00:00Z”}
- Run the Function
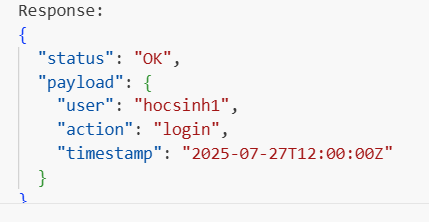
- With the TestLogin event selected, click Test.
- The execution result will be displayed below:
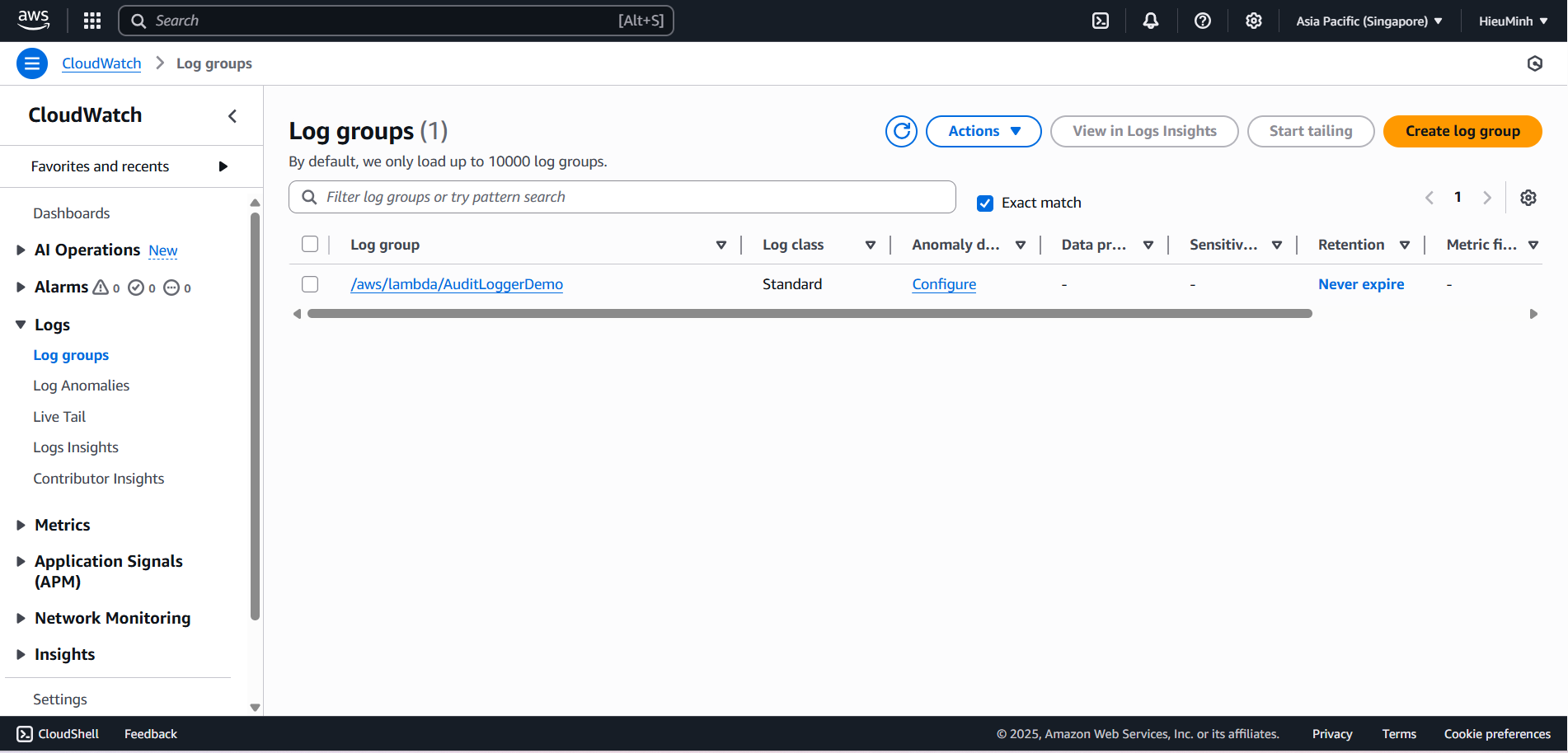
- Configure CloudWatch Logs
- Check the Log Group.
- Console > CloudWatch > Logs > Log groups > /aws/lambda/AuditLoggerDemo.
- Each invocation will create a new log stream.
- Create Metric Filter (…)